In the realm of digital security, the phrase “sorry, no manipulations with clipboard allowed canvas” underscores the importance of safeguarding sensitive information within the canvas of applications. This concern often arises in contexts where the manipulation of data via the clipboard poses potential risks to document integrity and confidentiality. Let’s delve into the subject, exploring step-by-step considerations, utility, and additional insights into the mechanisms employed to enforce these restrictions.
Step 1: Identifying the Need for Restriction
The initial step involves recognizing the necessity for restricting clipboard manipulations within the canvas. This could be driven by concerns related to unauthorized copying and pasting of critical information, ensuring that the content within the canvas remains secure and tamper-proof.
Step 2: Implementation of Clipboard Restrictions
To address this concern, developers and security experts employ various mechanisms to limit clipboard manipulations. This may involve coding restrictions within the application’s source code, utilizing security protocols, or integrating third-party tools designed specifically for controlling clipboard access.
Step 3: Canvas Security Protocols
Canvas security protocols play a pivotal role in enforcing restrictions related to clipboard manipulations. These protocols often include encryption measures, user authentication mechanisms, and access control policies to prevent unauthorized access to clipboard functions.
Step 4: User Education and Awareness
An essential aspect of implementing clipboard restrictions in the canvas involves educating users about the reasons behind such security measures. User awareness campaigns can highlight the risks associated with unchecked clipboard manipulations, fostering a sense of responsibility among individuals interacting with the canvas.
Step 5: Integration with Access Management Systems
Effective implementation of clipboard restrictions necessitates integration with access management systems. This ensures that only authorized users with the appropriate permissions can interact with the clipboard functions, reducing the likelihood of data breaches and unauthorized information sharing.
Additional Information
Balancing Security and Usability
While restricting clipboard manipulations is crucial for document security, developers must strike a balance between security measures and user convenience. Overly stringent restrictions can hinder user experience and workflow efficiency. Therefore, continuous assessment and refinement of security protocols are essential to meet evolving threats while maintaining optimal usability.
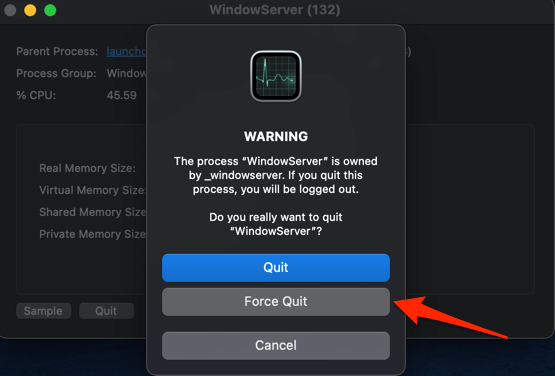
Why does it show “Sorry no manipulations with clipboard allowed”?
One of the major reason it shows sorry no manipulations with clipboard allowed is due to lots of load on the Mac. As you know we happen to open a lot of websites sometimes if we are into research or we are finding some articles for ourselves. However, many websites in the background process and due to this the processors are at their full capacity that is why we get this error.
Another reason to the sorry no manipulations with clipboard allowed error is due to third-party applications. There might be some file which does not comply with the default mac application which causes this error. However, it is recommended by the TechLogitic team to install Mackeeper to avoid such things in the near future.
However, closing unnecessary websites and monitoring third-party can help you get rid of sorry no manipulations with clipboard allowed error.
How does Clipboard partaking Works?
Once you’ve facilitated the flag, you’ll find a new-fangled “Copy to your device” selection when you right-click highlighted transcript on a web page. It’ll register all the devices with the flag facilitate that you’re signed hooked on through your Google account—on Windows, macOS, Linux, Chrome OS, in addition to Android. Select a piece of equipment to dispatch text unswervingly to its clipboard.
How to permit Clipboard Sharing?

This out of sight feature is to be had as a flag. To come across it, unbolt a new tab, paste chrome://flags into Chrome’s Omnibox and then force down the Enter key. Search for “Clipboard” in the investigation box.
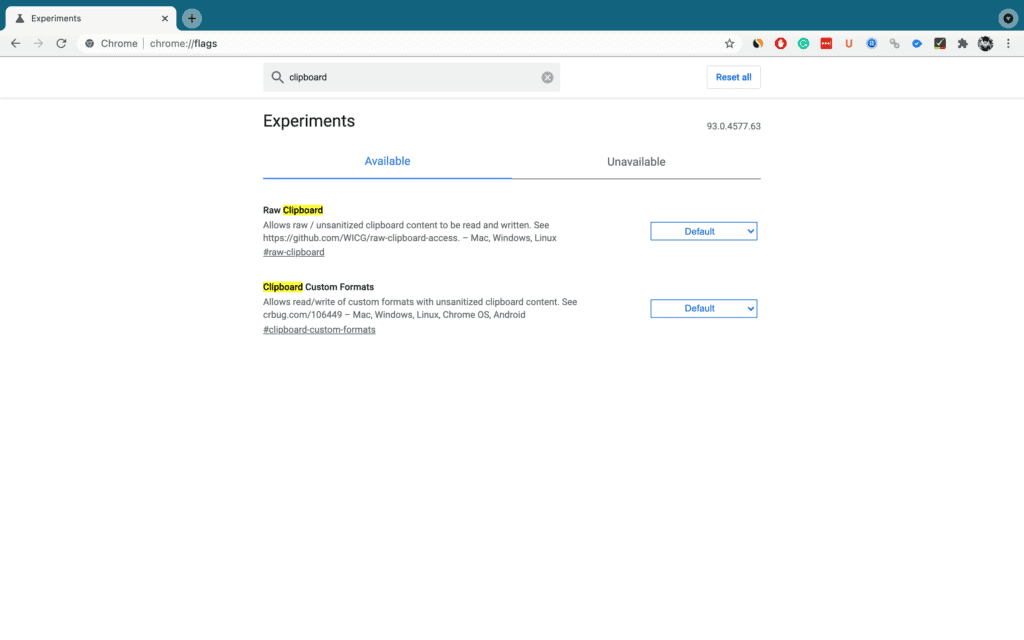
- Each flag handles poles apart part of this characteristic and needs to facilitate to function accurately.
- Enable all three alternatives.
Note: On Android, you will simply observe the “Enable receiver device to handle shared clipboard feature” in addition to “Enable shared clipboard feature signals to be handled” flags.
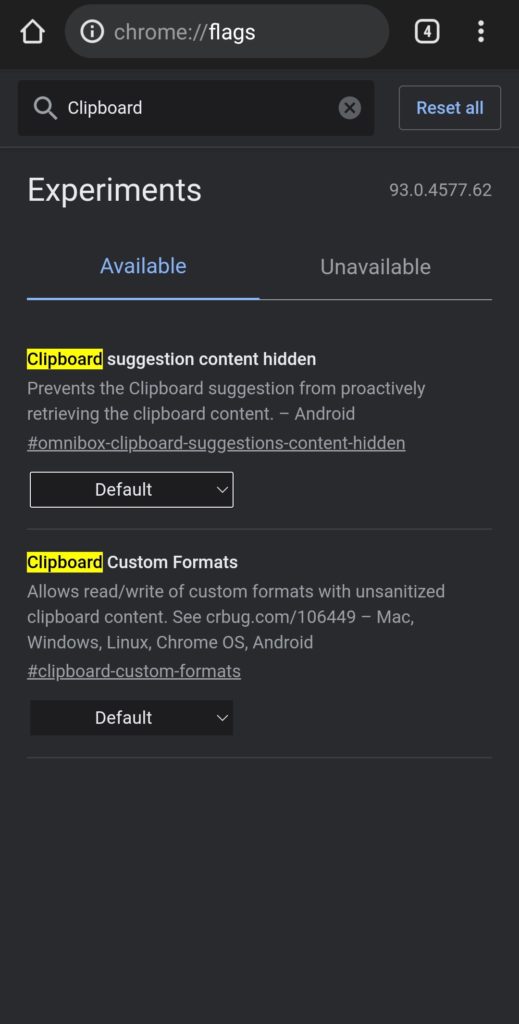
- When you’re done, sink in the “Relaunch Now” button to start again your Chrome browser by means of the flags enabled.
- Replicate this development on all devices that you make use of Chrome as a browser and wish to copy the manuscript onto the device’s clipboard.
How to reproduce Text Between Devices?
After enabling the flags and resuming your web browser, you’ll be intelligent to admission the characteristic from the right-click circumstance menu.
- Highlight some manuscripts from a web sheet and right-click on it to exhibit the context menu.
- Click “Copy to your devices” and prefer a device from the list.
- You’ll see a diminutive announcement in the Omnibox when you transmit some transcript to the other device.
- An announcement will appear on the erstwhile device, too.
- After copying the text copied to the apparatus, right-click—or long-press on Android—and prefer “Paste,” like you would with whatever thing on the clipboard.
If you don’t distinguish one of your devices in the inventory here, ensure it’s running the most recent version of Google Chrome with these flags facilitated and that you’re signed in to the equivalent Google account on all of your devices.
In this approach, the whole course of action is finished without many efforts and you have fruitfully copied the passage to another clipboard devoid of any trouble.
In conclusion
The repeated phrase “sorry, no manipulations with clipboard allowed canvas” underscores the commitment to securing digital content within the canvas environment. By following a systematic approach, implementing robust security measures, and fostering user awareness, developers and organizations can create a secure canvas that protects against unauthorized clipboard manipulations, ensuring the confidentiality and integrity of valuable information.